Does your organization do all that is required to ensure information security and cybersecurity?


Do you experience security breaches, or do you need to demonstrate to your customer or clients compliance with certain Information Security Management Standards?
The new ISO 27001:2022 Information Security Management System standard, also known as ISMS is the international standard that sets out the specification for an ISMS (Information Security Management Systems) recognized all over the world. Its best-practice approach helps organizations to manage and maintain their information security ensuring that they are addressing security of their people and processes as well as technology.
An ISMS is a holistic approach to securing the CONFIDENTIALITY – INTEGRITY – AVAILABILITY (CIA) of corporate information assets.
It consists of policies, procedures and other controls involving people, processes and technology.
Informed by regular information security risk assessments, an ISMS is an efficient, risk-based and technology-neutral approach to keeping your information assets secure. See the video below, how risk management requirements in ISO 27001:2022 can be managed…
BENEFITS OF IMPLEMENTING ISO 27001:2022
ISO 27001 is the most highly regarded information security standards in existence. Independently accredited certification to the Standard is recognized around the world and its popularity has grown in the ANSI National Accreditation Board (ANAB) by more than 450% in the past ten years. Implementing ISO 27001 helps you meet the legal information security requirements in the USA:
DATA PROTECTION, PRIVACY LAWS, NIST, NETWORK AND INFORMATION DATA PROTECTION & CMMC.
• Having implemented ISMS controls helps to reduce the costs associated with data breaches;
• It protects your data, wherever it lives;
• It protects all forms of information, whether digital, hard copy or in the Cloud;
• It increases your organization wide attack resilience;
• It increases your organization’s resilience to cyberattacks;
• It also reduces information security costs;
The new ISO 27001:2022 – All changes at a glance
The new ISO 27001 is finally here. In this ISO 27001:2022 update report you will get to know all the major changes of the revisions.
After ISO 27002:2022 had already been updated as a guide for information security management, the catalog of measures (Annex A) of ISO 27001:2022 in particular has now changed as a result as well. This contains a list of possible information security measures and was derived from the revised standard ISO/IEC 27002:2022.
The updates to ISO 27002 that have already taken place include a reduction in the main classification from 14 to 4 main areas.
In addition, 12 new controls have been added.
Many of the existing controls have also been renamed to better describe their respective tasks.
Lets get you aquainted with the various innovations. We also want to show you how to implement the new requirements in an internal Information Security Management System (ISMS). Finally, you will also know how to manage information security risks after updating the ISO/IEC 27001:2022 standard and ISO/IEC 27002:2022.
The first thing that stands out is that the title of ISO 27001:2013 has changed.
The new ISO version is called “Information Security, Cybersecurity and Data Protection – Information Security Measures”.
Cyber security, as well as the inclusion of data protection in the name, is new. The addition is not surprising for us, since information security and data protection – even if they take different perspectives – pursue very similar goals and are implemented cooperatively at best.
Innovations of the new ISO 27001:2022 Annex
The annex to the new ISO 27001:2022 deals with the essential changes for information security, cybersecurity and privacy protection – information security management systems – requirements. Among other things, this part of the new ISO 27001 deals with the security measures and their attributes. The structure and content of the new controls from Appendix A has also changed:
• 4 main categories (instead of 14) – organizational controls, personnel controls, physical controls, technological controls
• 93 security measures (instead of 114)
• 5 Attributes of Security Measures – Control Type, Information Security Characteristics, Cyber Security Concepts, Operational Capabilities, Security Domains
The 4 main categories:
• Organizational controls (37 measures)
• People controls (8 measures)
• Physical controls (14 measures)
• Technological controls (34 measures)
11 measures have been added in the new ISO27001:2022:
• A.5.7 Threat intelligence
• A.5.23 Information security for use of cloud services
• A.5.30 ICT readiness for business continuity
• A.7.4 Physical security monitoring
• A.8.9 Configuration management
• A.8.10 Information deletion
• A.8.11 Data masking
• A.8.12 Data leakage prevention
• A.8.16 Monitoring activities
• A.8.23 Web filtering
• A.8.28 Secure coding
In addition to the new measures and the new structure, each measure is now classified into five different attributes:
• Control Type
• Property of information security
• Cyber security concepts
• Operational Capabilities
• Security Domains
All transition periods at a glance
ISO 27001:2022 was published on October 25, 2022. The transitional period has been set at three years (36 months).
This results in the following transition periods and deadlines for standard users. Certifications can be carried out from February – April 2023.
For companies that are already certified, this means adapting and updating the existing ISO documentation for the new controls as early as possible. Especially for business continuity management. The requirements for documentation have become stricter here. At the next audit, the company can already be certified according to ISO 27001:2022.
Mapping the new ISO27001:2022 with the old 2013 version
For a better understanding, JJK Consulting provides certified gap assessment audits, training, and consulting to perform gap assessments on your existing ISMS activities in comparison to the new ISO 27001:2022 requirements. So you can see directly what has changed.
Best Practice Implementation
Choosing JJK CONSULTING as your implementation partner, ensures your organization will implement only the security controls you really need, helping maximize your budget.
Our ISMS experts are all ISO27001 certified Lead Auditors with many years of implementation experience and can make sure, that you will respond to evolving security threats in the best ways. This will lead to a more agile organization, one in which you can constantly adapt to changes externally and within the organization. Improved information security and company culture is the outcome.
An ISMS encompasses people, processes, and technology, ensuring staff understand risks and embraces security as part of their everyday practice. If meeting contractual obligations or demonstrating ISO 27001:2022 Certification to your customers is required, you will be able to do so, by easily demonstrating your organization’s commitment to information security.
This provides a valuable credential when seeking new business opportunities.
HOW TO ACHIEVE COMPLIANCE TO ISO 27001:2022
JJK CONSULTING is here for your organization to help you implement an ISO 27001-compliant ISMS. Our effective and budget friendly “hands-on” implementation services involve…
• SCOPING THE PROJECT
• Securing management commitment and budget;
• Identifying interested parties, and legal, regulatory, and contractual requirements.
• Conducting a risk assessment;
• Reviewing and implementing the required controls;
• Developing internal competence to manage the project;
• DEVELOPMENT OF YOUR APPROPRIATE ISMS DOCUMENTATION
• Reporting (e.g. the Statement of Applicability and risk treatment plan);
• Continually measuring, monitoring, reviewing, and auditing the ISMS; and
• Implementing the necessary corrective and preventive actions.
• And finally CONDUCTING STAFF AWARENESS TRAINING
This way your organization will be ready for ISO Certification Audit soon.

GET ISO 27001:2022 CERTIFIED ON TIME & BUDGET
We offer everything you need to implement an ISO 27001-compliant ISMS – you don’t need to go anywhere else.
We guarantee certification (provided you follow our advice!).
You benefit from real-world practitioner expertise, not just academic knowledge.
We have a proven and pragmatic approach to assessing compliance with international standards, no matter the size or nature of your organization.
Our pricing and proposals are completely transparent, so you won’t get any surprises.
We can help small organizations prepare for ISO 27001 certification in three months.
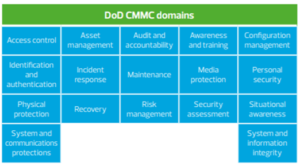
The US Department of Defense (DoD) has developed a new certification framework to address cyber risks in supply chains. The new “Cybersecurity Maturity Model Certification” (CMMC) establishes a 5-stage maturity approach for cybersecurity requirements. From June 2020 onwards, the requirements are to be established as part of Sections L and M of the “Request for information” (RFI) and in the tendering process from around September 2020 onwards.
Now let’s read on about the most important aspects of the CMMC and what is necessary to coordinate security processes, specifications and practices in compliance with the CMMC. The CMMC offers the DoD an instrument to enforce the current Defense Federal Acquisition Regulation Supplement (DFARS) requirements (DFARS clause 252.204-7012) in your contracts. Functionally, the CMMC is based on various standards, such as ISO 27001:2013, but has the highest degree of coverage with the “National Institute of Standards and Technology Special Publication 800-171”, the current standard for the protection of “controlled unclassified information” (CUI ).
What to do when my organization is working on the requirements from DFARS or NIST SP 800-171?
Organizations that already meet the requirements of NIST SP 800-171, are in a good position to look after certification of the CMMC Level 3. 130 controls are congruent with those of NIST SP 800-171; however, there are still 20 different controls in CMMC Level 3 added…
• Identification, classification – Identification of information
• Storage and analysis
• Audit Logs
• Event management
• Incident management
• Storage of backup data and Perform recovery tests
• Conducting code reviews In software development
• Cyberthreat Intelligence Management
• Network security
• Implementation of DNS filtering
• Use of email security (Spam filter, encryption, etc.)
How should organizations prepare for the CMMC?
If you are currently working with the DoD or will do so in the future structured preparation is essential. Even if still not everything about the CMMC is finalized, so many are already central Information and requirements are available on the DoD’s publications. The information are sufficient to prepare for the expected finalization of the framework in autumn 2020 to prepare.
With this in mind, we recommend the following steps over the coming weeks and months initiate:
• Identification of the information that is subject of the DoD contract and their complementary Processes, Systems and Applications. Consolidation this to reduce the “compliance footprint”.
• If you use CUI or “covered defense information” (CDI) yourself and already meet the requirements from DFARS which you need to follow, you should focus on at least one.
Set up for Level 3 certification.
• Carry out a detailed gap analysis to determine the current level of maturity and identify any gaps.
• Develop a roadmap to get the gaps structured close.
• As a subcontractor, you should look after your customers approach and find out whether this is already received information regarding CMMC.
How can JJK Consulting support your organization?
• analysis of information, processes and systems to identify the scope
• Assessments to determine the current degree of maturity and any gaps
• Development of a roadmap to fill gaps in a structured manner close & enable a higher degree of maturity
• Establishment of “security controls” and processes based on the required level
Our cybersecurity experts are happy to support you.
Ready to Explore New Possibilities?

Please contact JJK Consulting at your convenience for an initial consultation.
We’ll work with you one on one to determine a roadmap to success.
Call Today: 973-402-5889