Does your organization do all that is required to ensure information security?
Do you experience security breaches, or do you need to demonstrate to your customer or clients compliance with certain Information Security Management Standards?
ISO 27001:2013 Information Security Management System standard, also known as ISMS is the international standard that sets out the specification for an ISMS (Information Security Management Systems) recognized all over the world.
How to set up Information Security Management System based on ISO27001:2013?
An ISMS is a holistic approach to securing the CONFIDENTIALITY – INTEGRITY – AVAILABILITY (CIA) of corporate information assets.
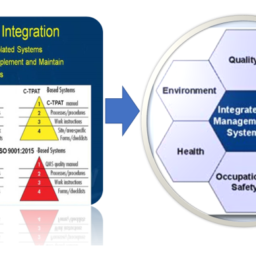
It consists of policies, procedures and other controls involving people, processes and technology.
Informed by regular information security risk assessments, an ISMS is an efficient, risk-based and technology-neutral approach to keeping your information assets secure.
The Standard outlines 14 control categories with 114 standard information security management system controls but does not mandate that all 114 controls be implemented. Instead, the risk assessment should define which controls are required, and a justification provided as to why other controls are excluded from the ISMS.
ISO 27001:2013 – ANNEX A – THE 14 CONTROL CATEGORIES
• A.5 Information security policies
• A.6 Organization of information security
• A.7 Human resource security
• A.8 Asset management
• A.9 Access control
• A.10 Cryptography
• A.11 Physical and environmental security
• A.12 Operations security
• A.13 Communications security
• A.14 System acquisition, development and maintenance
• A.15 Supplier relationships
• A.16 Information security incident management
• A.17 Information security aspects of business continuity management
• A.18 Compliance
BENEFITS OF IMPLEMENTING ISO 27001:2013
ISO 27001 is the most highly regarded information security standards in existence. Independently accredited certification to the Standard is recognized around the world and its popularity has grown in the ANSI National Accreditation Board (ANAB) by more than 450% in the past ten years. Implementing ISO 27001 helps you meet the legal information security requirements in the USA:
DATA PROTECTION, PRIVACY LAWS, NIST, NETWORK AND INFORMATION DATA PROTECTION & CMMC.
• Having implemented ISMS controls helps to reduce the costs associated with data breaches;
• It protects your data, wherever it lives;
• It protects all forms of information, whether digital, hard copy or in the Cloud;
• It increases your organization wide attack resilience;
• It increases your organization’s resilience to cyberattacks;
• It also reduces information security costs;

BEST PRACTICE IMPLEMENTATION
Choosing a “Hands-On” expert from JJK Consulting as your cost effective implementation partner, ensures your organization will implement only the security controls you really need, helping maximize your budget.
Our ISMS experts are all ISO27001:2013 certified Lead Auditors with many years of implementation experience and can make sure, that you will respond to evolving security threats in the best ways. This will lead to a more agile organization, one in which you can constantly adapt to changes externally and within the organization. Improved information security and company culture is the outcome.
An ISMS encompasses people, processes, and technology, ensuring staff understand risks and embraces security as part of their everyday practice. If meeting contractual obligations or demonstrating ISO 27001:2013 Certification to your customers is required, you will be able to do so, by easily demonstrating your organization’s commitment to information security.
This provides a valuable credential when seeking new business opportunities.
“We are helping our clients build best practice information security management systems (ISMS) 100% integrated in their existing management systems, this enables our clients to achieve highest standards in information security and ensures that any client requirement for information security is covered to avoid set backs during the acquisition process. This has been very beneficial for our clients, as the markets are very competitive, especially during these challenging pandemic times” says Jim Kachidurian, President of JJK Consulting. He adds: JJK Consultants are all experienced experts and certified lead auditors in ISO27001:2013 with hundreds of audits on their belt, they represent the very best in the field. These information security experts create effective and efficient Integrated Management Systems inclusive coverage of Cybersecurity issues and can help every organization to establish 3rd party audit readiness for its ISMS very effective on time and budget”.
CYBERSECURITY MATURITY MODEL (CMMC)
Here are the latest information and status on the new CMMC framework required by the U.S. government in 2020. CMMC Certification is only required for existing contracts with the government, within any new RFI / RFQ starting in Oct 2020.
Here are the latest updates…
CMMC 1.0 (Released 01/2020) requires control of Controlled Unclassified Information (CUI) already in Level 2 – Federal Controlled Information (FCI) is not enough for winning contracts with the government anymore.
DFARS (Red sections) / CMMC and NIST requirements overlap strongly – it all depends on the RFQ / contract starting from 10/2020.
CMMC LEVEL 3 REQUIREMENTS
For CMMC Level 3 – “upgrades” must be done from existing NIST 800-171 management systems including new Backup + Restore requirements, new DNS Filtering controls, Isolation + Support Platforms control, enhanced Spam Email Protection, and several other new “features”.
Our current CMMC Gap audits at organizations showed the following gaps for compliance to CMMC Lev 3…
-No official Change management in place (Missing Change Log, Control of Configuration of Environment, etc..)
-No CUI Data Flow Control Diagrams in place (Visual on how flows the data in the company)
-No Risk Treatment Plans in place
-No internal Audit Logs in place / SIM event categories, Severities, SIM User Authentication, etc.
-No Black / White listing of SW in place
Workstations + Server Configuration has not been implemented according to NIST 800-171.
For CMMC Lev 3 – A System Security Plan (SSP) and a Plan of Action and Milestones (POA&M) is a must – but there cannot be action items against CMMC Lev 3 – only enhancements/improvements towards Lev 4 + 5 are allowed.
Tip: Valid CMMC audit compliance evidence needs to be valid and provided NOT BEFORE Contract award – use the time and get compliant to your level of CMMC requirement. Let an ISO27001:2013 and CMMC expert like e.g. from JJK Consulting evaluate your status of compliance early enough, so you can be sure to have your compliance status ready, when its the time.
FUNDING
There might be Federal or state wide funding for establishing a ISO27001:2013 and/or CMMC Lev 1-3, Framework in your organization.
JJK Consulting can remediate all issues within 100% compliance to ISO27001:2013 and CMMC Level 1-5 Certification and investigate for any funding option in our state. For more information and a complimentary investigation on your customized funding options, please contact our HQ in New Jersey.
GET ISO 27001:2013 CERTIFIED ON TIME & BUDGET
JJK Consulting offers everything you need to implement an ISO 27001:2013 and CMM compliant ISMS – you don’t need to go anywhere else. We guarantee certification (provided you follow our advice!). You benefit from real-world practitioner expertise, not just academic knowledge.
We offer ISO 27001:2013 and/or CMMC Certification – Implementation – Audit Service – Training – Services available in the NY Metro Area and Nationwide Onsite or within Remote/VPN secure teleconference meetings.
Ready to Explore New Possibilities?
 Please contact JJK Consulting at your convenience for an initial consultation on ISO 27001:2013 and/or CMMC Certification.
Please contact JJK Consulting at your convenience for an initial consultation on ISO 27001:2013 and/or CMMC Certification.
We’ll work with you one on one to determine a roadmap to success.
Call Today: 973-402-5889
#iso27001certification #cybersecurity #informationsecurity